Laura Wilkinson and Professor Dale Rowe, Information Technology
Introduction
A study done by the University of Singapore reports that in 2014 alone, $491 billion dollars was spent repairing damage dealt by Malware. Many of the companies hacked occurred because of Malware on the Point of Sale (POS) machines, which collected credit card information. Besides wreaking havoc on companies, Malware presents a big problem with infrastructure systems. In 2010, a virus called Stuxnet was identified that ultimately was responsible for the destruction of 1/5 of Iran’s Nuclear Centrifuge. Because of this the need to detect malware before it can do damage is of high importance.
Originally, the plan was to utilize an analysis of behaviors of unknown programs to essentially ‘guess’ if it was malicious or benign, but we quickly figured out that current environments were not suitable for studying live malware. Malware can spread quickly and cause damage while studying it. Ultimately we were missing a step that needed to be resolved before we could continue studying the malware. We switched gears in order to produce an environment that was capable of studying malware while protecting all the systems around it.
Methodology / Results
We wanted to create an environment where the malware wouldn’t spread, and should the malware infect the system being used to study it, we could reset it quickly without having to reinstall everything. For this we turned to virtual technologies. The ability to spin up a cloned Virtual Machine (VM) when things go wrong was very important. We designed a system where storage of the virtual machines were contained on servers located other than the classrooms and students could access them through a browser, thus keeping possible infection from spreading through the labs. This would be known as the ‘infection zone.’
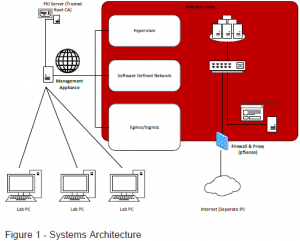
A lot of malware only tend to react when connected to a network because they connect back to a commanding server. A virtual network works just like a physical network, and is bridged with physical networks, and as such the threat of spreading even though it was being studied on ‘throw away’ machines still exists. Software Defined Networks (SDNs) provide a way to isolate different networks, and allow instructors and team leads to maintain complete control over the network between the virtual machines. These network IP ranges were set on separate and isolated subnets from the rest of the network connections. Campus IT is alerted to these ranges.
The last point in which we needed to be really careful with is the direct connection with campus internet. This is where we implemented specific filters called Ingress and Egress. We had specialized firewalls that were monitoring all the traffic. Any traffic trying to go to unauthorized places set off alarms.
Conclusion
As a result of this design, we had several new deliverables. A paper on the methodology was accepted by the IAJC Annual Conference, and was also accepted for publication in 2015 by the TIIJ. From this paper, a new class on malware analysis for the Cybersecurity program was developed. We envisage expanding the architecture to allow for network layering between the analysis VMs and the egress/ingress firewall. This would allow the insertion of in-line network devices such as intrusion detection systems, honeypots and traffic emulators. It would also facilitate research into the effectiveness of such devices in a malware detection and mitigation scenario. New malware techniques could render current environments useless, and we believe this could be utilized into the future, and provide us with the space to continue with the previous project in a safe environment.
