Craig Treasure and Dr. Chia-Chi Teng, School of Technology
Current medical imaging technology exists in the form of large and expensive systems in hospitals inside the network firewalls. Data from these machines is only transmitted on a hospital’s computer network to maintain the privacy of patient’s personal information and images. These expensive machines require high processing power to process medical images to be used by physicians and doctors. Patient’s data is protected by keeping it within the hospital’s private computer network.
The costs of building and maintaining these medical imaging networks can be dramatically reduced by offloading the image processing to servers on the internet known as cloud services. Many hospitals use medical imaging equipment that is unavailable to small clinics and underprivileged areas or third world countries due to the costs of that equipment. By moving the storage and processing portion of the equipment to a cloud server, clinics can use inexpensive commercial devices to send medical images and data to a cloud server to be processed and then viewed from a web interface.
By providing a secure connection for devices or software to use when transmitting data, medical clinics can realistically and securely use inexpensive commercially available devices with a cloud service to process and view medical images. They will be able to do so resting assure that the cloud service complies with The Health Insurance Portability and Accountability Act of 1996 (HIPAA), which requires the protection of patient data. By addressing this problem, smaller clinics and under privileged populations in remote areas or third world countries can experience more effective and more affordable health care.
The purpose of this research is to study what security techniques are required to keep patients images and data secure while transmitting them across the internet and how that security may impact the performance of that transmission.
A project led by Dr. Chia-Chi Teng called MIMIC1 was created using Microsoft’s Azure cloud platform in 2009 to provide a DICOM server in the form of a cloud service. The server conforms to DICOM standards by utilizing the DICOM# .NET library and has been tested with existing DICOM standard client applications using insecure connections. A new client application was created utilizing the MDCM .NET library for DICOM standards support to test and build a DICOM SSL implementation. Neither the DICOM# library nor the MDCM library support communications via SSL which required the libraries to be updated with a Microsoft .NET implementation of a secure connection using a set of secure socket layer (SSL) certificates that are held by both the server and the client.
To develop this solution, SSL implementations for both MDCM and DICOM# were done and SSL certificates were generated using Microsoft Internet Information Services Manager. Certificates generated by a trusted CA (Certificate Authority) such as VeriSign or DigiCert
would also work.
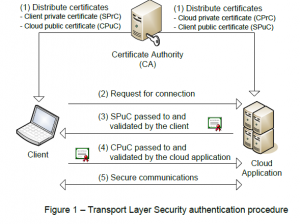
Figure 1 shows the high-level TLS two-way authentication procedure. The simplified process is as follows:
- Creation & distribution of certificates by the trusted CA to setup both cloud application and client.
- The client requests for a connection from the server.
- The server responds with its public certificate, SPuC. The client checks if the SPuC identifies the trusted cloud server.
- If the SPuC passes the test, the client responds with its public certificate, CPuC. The server verifies that the CPuC is from a trusted client according to the validation procedure.
- If the CPuC passes the test, a symmetric key is used to encrypt the remainder of the communication session.
As with any SSL communications, a performance penalty is incurred due to the overhead of the security layer. To examine the performance difference the new SSL communications causes, a network packet analyzer called Wireshark was used to measure the time it takes to complete the protocol. It was found that it took an average of 7 seconds when the communication was not secured and 9 seconds when it was secured. This shows the expected increase in time resulted from the overhead of securing the communications.
This research has proven that it is possible for a medical imaging server placed on a public cloud infrastructure to provide secure communications with its clients as required by HIPAA rules and regulations. To further prove the viability and cost effectiveness of the solution, the project was presented in the Microsoft Imagine Cup 2011 national competition with team BearPaw. The project was very successful and was further presented at a national developer’s conference in Atlanta, Georgia.
References
- Chia-Chi Teng; Mitchell, J.; Walker, C.; Swan, A.; Davila, C.; Howard, D.; Needham, T.; “A medical image archive solution in the cloud,” Software Engineering and Service Sciences (ICSESS), 2010 IEEE International Conference on , vol., no., pp.431-434, 16-18 July 2010