Scott Heidbrink and Faculty Mentor: Daniel Zappala, Computer Science
Introduction
While there is a long tradition of providing protection against attackers for desktop and laptop devices, there has been less work in the mobile space. A common tool used by antivirus software is to inspect all packets entering or leaving a computer, to check for viruses or other malware. There are currently no generalpurpose tools for Android devices that provide for packet inspection and modification. There are a few tools that allow for packet capturing on mobile devices, but they can only function on “rooted” devices and do not allow modification. Since most users do not “root” their devices, these tools have limited utility. There also exists only one application, tPacketCapture, that allows unrooted devices to capture network data. However, it does not provide a mechanism to modify packets. Furthermore it is not open source, preventing widespread adoption by other developers and researchers.
A general purpose library for packet inspection and modification provides numerous opportunities for security enhancements to the Android platform. Such as developing a certificate authentication middleware. This can help deployment and adoption of new authentication services to improve current Certificate Authority authentication weaknesses and help to insure correct certificate validation for all SSL traffic.
We created both a packet inspection and modification tool for Android and demonstrated its usefulness by creating a certificate authentication middleware.
Methodology
Using Android’s VPNService, we were able to create an application that can intercept and modify any IP packet to and from an unrooted Android device. Because of limitations from the VPNService, the Android restrictions on Java, and that we wanted our system to run on unrooted 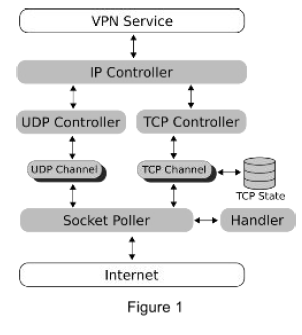 devices we had to create a pseudo implementation of IP, TCP, UDP, and for an example of the usefulness of our app TLS. Shown in Figure 1 is a diagram of our implementation. We receive an IP packet from the VPNService that is then parsed by the IP controller and it’s respective transport layer controller, TCP or UDP, which handle any necessary state and finally is sent to the internet through a separate Java socket that we create so that we may modify the payload.
devices we had to create a pseudo implementation of IP, TCP, UDP, and for an example of the usefulness of our app TLS. Shown in Figure 1 is a diagram of our implementation. We receive an IP packet from the VPNService that is then parsed by the IP controller and it’s respective transport layer controller, TCP or UDP, which handle any necessary state and finally is sent to the internet through a separate Java socket that we create so that we may modify the payload.
We also implemented what is known as TrustBase, a certificate authentication middleware, that allows for inspection of SSL traffic and dynamic certificate authentication through the use of plugins.
Results
The most important result we believed is whether our system would be usable. We tested connection times and downloading various sized files under normal phone conditions, running our packet inspection app, and running our TrustBase middleware. The results are given in Figure 2. When TrustBase 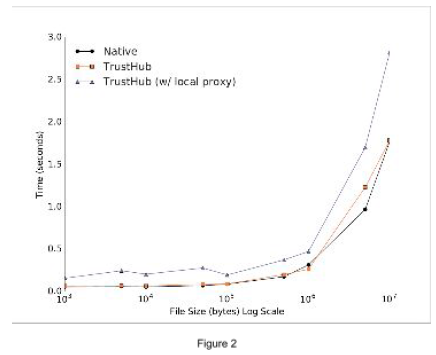 determines that a connection needs to be proxied, so that correct SSL authentication can take place, it can almost double the download times. With just our packet inspection app timings are comparable to native timings.
determines that a connection needs to be proxied, so that correct SSL authentication can take place, it can almost double the download times. With just our packet inspection app timings are comparable to native timings.
Discussion
The results of our download experiments show that creating an app that allows for Android packet inspection and modification requires little overhead and is possible on an unrooted Android device. This can allow for the development of more security related application on mobile devices.
To demonstrate this we created a certificate authentication middleware where authentication plugins can be created to authenticate SSL traffic in a dynamic manner. The overhead of such an app, as our results show, can get high, but provide a greater amount of security. Other less intensive security applications can also be developed on top of our packet inspection and modification tool, or diagnostic apps such a wireshark type app to help better analyze mobile network problems.
Conclusion
The packet inspection and modification tool we developed is a much needed addition to mobile software and can allow for development of greater security in the mobile space, such as through our certificate authentication middleware.
