Shane K. Curtis and Dr. Christopher Mattson, Mechanical Engineering
Main Text
Reverse engineering is a prominent design strategy in industry, employed by many to uncover the enabling technologies of innovative products. Unfortunately, there is little motivation for original designers to create new products if competitors can reverse engineer these products and reproduce them at a lower development cost. One solution to this problem involves the incorporation of barriers to reverse engineering into products during the design process. These barriers not only increase the cost of reverse engineering but can also improve product performance with only a small increase in manufacturing or development time.
Perhaps the most effective method to prevent reverse engineering is to prevent competitors from obtaining a product. However, this is simply not feasible for commercial products where the goal is to sell the product to as many consumers as possible. Likewise, it is not practical to integrate barriers to reverse engineering into every feature in a product4. The method presented herein helps to identify the critical component(s) in a system, allowing designers to focus their efforts and optimally build barriers to reverse engineering into a product to protect the most valuable information.
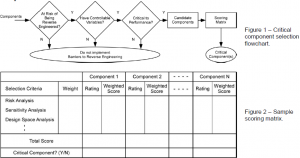
A summary of the critical component selection method is depicted as a flowchart in Figure 1. As shown, system components are the inputs to the process. Therefore, selection of critical components requires at least a partial understanding of the components in a system prior to beginning the process. A designer would then use the flowchart to evaluate every component, utilizing both designer intuition and numerical methods to efficiently and effectively find the critical component(s).
The first three decision boxes in Figure 1 function much like a product development screening process, removing unsuitable components from the candidate component pool without requiring extensive analysis. In the first box, a designer must assess whether or not a component is at risk of being reverse engineered. Clearly, if no one will reverse engineer a particular component, then spending resources to add barriers to reverse engineering would not serve a useful purpose. If the component is at risk, it continues forward in the flowchart; otherwise, it is removed from the candidate pool, and the designer begins the process again with a different component.
In the second box in Figure 1, a designer decides if the component has controllable variables. Often, barriers to reverse engineering can only be implemented if certain aspects of the component can be manipulated, such as yield strength or electrical conductivity. If the component cannot be modified, then it is probably not a good candidate for additional barriers to reverse engineering and it is removed from the pool.
At the third box in Figure 1, a designer decides if the component is critical to the overall system performance. This step does not require extensive analysis. Instead the goal here is to remove non-critical components based on designer intuition. If the designer determines that the component has a large impact on system performance, then it proceeds forward in the process.
Components that have survived the screening process are now considered valid candidate components for barrier implementation (see the fourth box in Figure 1). This set of components can be further reduced to find the critical component(s) during the next stage in the process, which is known as scoring. In the scoring phase, components are entered into a scoring matrix. An example scoring matrix is shown in Figure 2. The top row of the matrix contains the candidate components, while the first column on the left contains the selection criteria, which can be weighted to allow the designer to emphasize desired criteria. In the example matrix, the selection criteria includes risk analysis, sensitivity analysis, and design space analysis. While some of this analysis was qualitatively performed previously during screening, the designer must now rigorously evaluate each component. The results, which are quantitative in nature, are entered into the matrix in the rating column for each component, multiplied by the associated weight, and summed to determine the total score of each component. The component with the highest score is the critical component in the product or system.
At the conclusion of the critical component selection process, the optimal component for barrier implementation has been identified. Barriers to reverse engineering now need to be designed and developed for the critical component. For more information on barrier implementation, the author refers the reader to his own work on barriers to reverse engineering mechanical components.
References
- Mansfield, E., Schwartz, M., & Wagner, S. (1981). Imitation costs and patents: An emperical study. The Economic Journal , 91 (364), 907-918.
- Harston, S. P, Mattson, C. A., Adams, B. L., & Ahmadi, S. (2008). Capitalizing on heterogeneity and anisotropy to find designs with unexpected performance. In 12th AIAA/ISSMO Multidisciplinary Analysis and Optimization Conference, Victoria, British Columnbia, Canada, AIAA 2008-6015.
- McLoughlin, I. (2008). Secure embedded systems: the threat of reverse engineering. Proceedings of the 2008 14th IEEE International Conference on Parallel and Distributed Systems, pp. 729–736.
- Grand, J. (2004). Practical secure hardware design for embedded systems. Proceedings of the 2004 Embedded Systems Conference, San Francisco, California, March 29-April 1, 2004.
- Curtis, S. K., Mattson, M. A., & Harston, S. P. (2010). On barriers to reverse engineering mechanical components. In ASME 2010 International Design Engineering Technical Conferences, Montreal, Quebec, Canada, DETC2010-28610.
